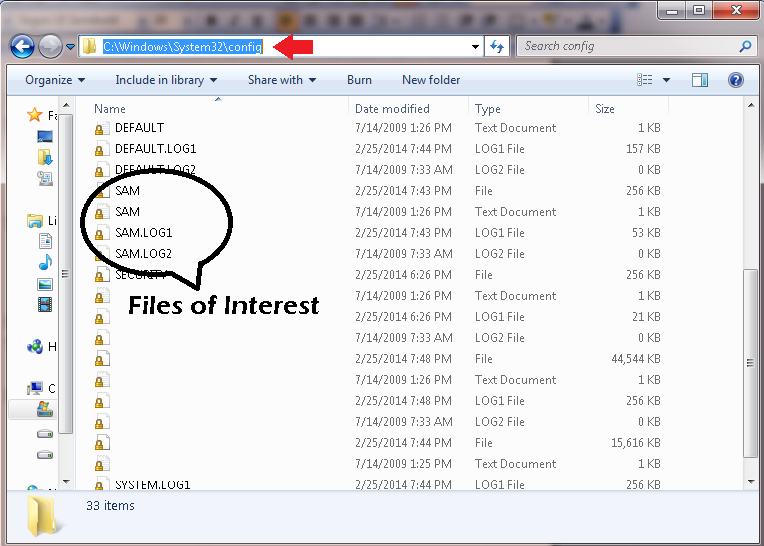
TCS Presents
Code Vita V3 2014
Coders Creed is pleased to inform you that
TCS has launched Code Vita 2014 after Code Vita 12 & 13 for all Engineering
and Science Graduates, this time 10+ countries are participating.
Eligibility Criteria
All students from Engineering and Science
Colleges can apply.
Registration is free and no other
eligibility is required.
How to apply?
Click down the
below link to start TCS Campus Commune Homepage.
> Register as New Candidate > Off
Campus Applicant (if your college is not accredited by TCS, mostly it’s not).
Important: If you can’t find your college name
in the institute list then select “others” option.
Once you are registered in Campus Commune
click the banner of Code Vita for Registering for the Competition.
Once you do so, you will acquire a secret
code (used to login in the Code Vita Site)
Last Date for Registration is 11
August 2014 in India
Form a team with 2 members from
the same institute. (1 Team Lead + 1 Member)
Structure of the Contest
• After
Registration the practice rounds will be open for the participants ( I highly
recommend to practice before Round 1 as much as you can)
• Round 1: Comprising programming problem
statements. Apart from selection of teams for the second round, the contest
will also help contestants warm up for the next round.
• Round 2: Top 5% of teams across Phase 1
geographies will move into this round.
• Grand Finale: Top 15 teams from Round 2
(both Phase 1 and Phase 2), will be invited for the Grand Finale, to be held in one of the TCSL
offices in India. Top 3 teams will be declared winners of the contest.
Your Code will be judged on the
basis of
1. Accuracy: How close a solution is to a
given problem statement
2. Speed: Time taken to solve the problems
3. Efficiency: Resources allocated to the
solution (CPU cycles, Memory)
The Code Vita is supporting 7 languages in
which you can submit your solution.
Languages with their compiler versions are
listed below:
Important Dates (Updated and extended)
$ So Brace Yourselves and Happy Coding ….